CIM Account Takeover
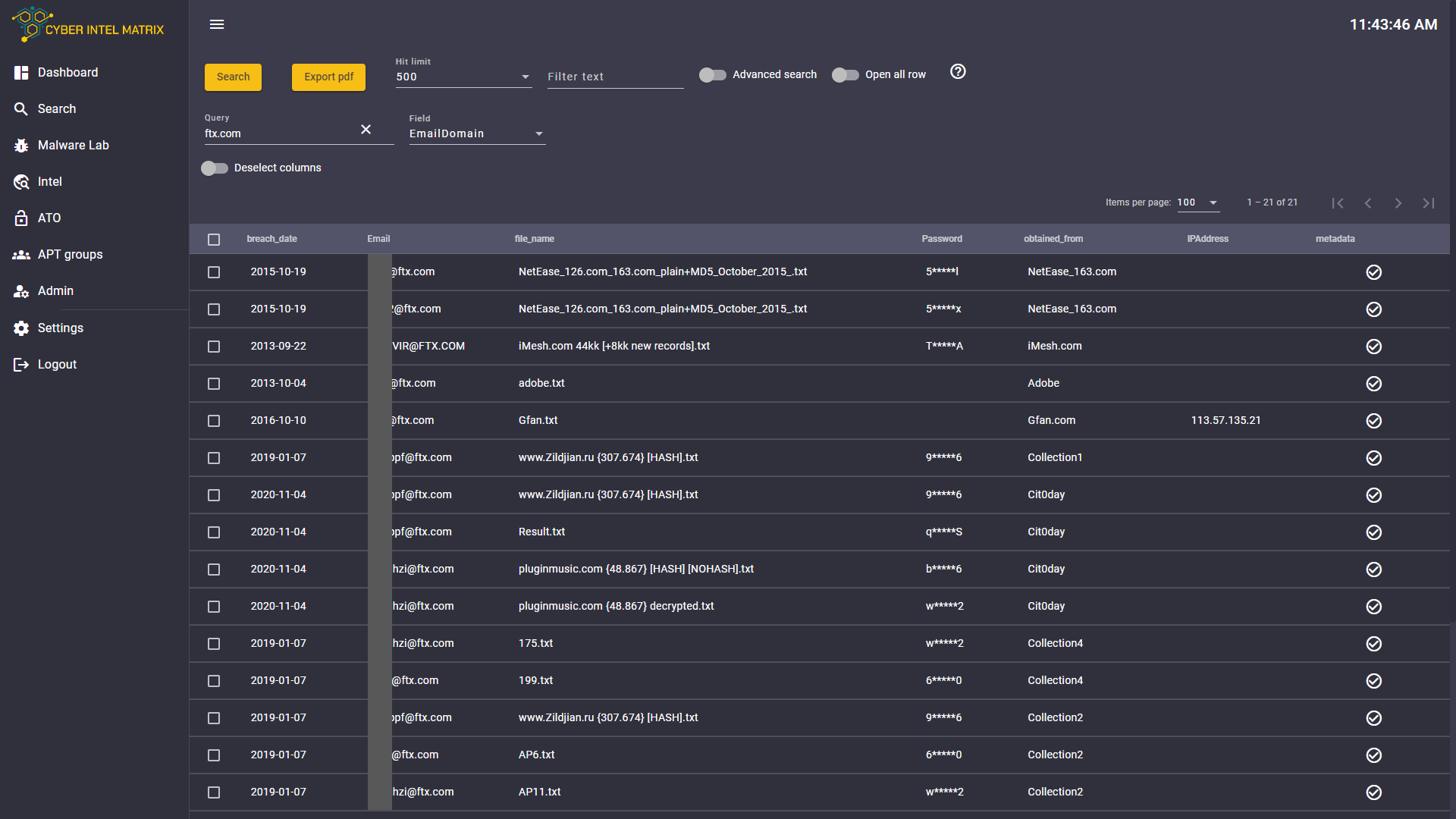
Account Takeover (ATO) is CIM’s Breached Credentials Database. CIM sources and procures access to an annotated virtual database of 25+ billion breached credentials (user names, passwords, phone numbers, addresses, IP numbers, email addresses), part of the CIM Framework, available as a separate service. Reveals leaked credentials in real time and other valuable PII used for social engineering.

Features
Real-time verification against an annotated 25+ billion breached credentials database
A breached credentials database, also known as a credential stuffing list, is a collection of usernames and passwords that have been stolen or leaked from various sources, such as data breaches or hacking incidents. These databases typically contain millions of credentials from a variety of websites, services, and platforms.
Criminals can use breached credentials databases for social engineering and to carry out credential stuffing attacks, which involve using automated tools to try large numbers of stolen usernames and passwords across multiple websites or services in order to gain unauthorized access to user accounts. The attackers are hoping that many users have reused the same username and password combination across different accounts, which is a common practice but a dangerous one.
All the fields in the records are searchable
- Email address
- User name
- Password
- Breach date
- Breach source
- File name
- IP address
- Meta data
- Physical address (Street, City, Zip, Country)
- Birth date
- Full name
- Phone number
- Last activity on breached server
- Registered on breached server
Advanced search & query options
Full-text search, Boolean operators, regular expressions, wildcards, and faceted search are available to make search efficient.
Historical data going back 12+ years
By using historical data from breached credential databases, cybersecurity professionals can gain valuable insights into the patterns and trends of credential reuse, and use this information to help prevent future data breaches and credential stuffing attacks. They can also use historical data to help users identify whether their credentials have been compromised in past breaches and take steps to secure their accounts.
Passwords intentionally masked
CIM applies a strict compliance regime under the laws and regulations that govern the handling, processing, and public display of personally identifiable information (PII) data, designed to protect individuals’ privacy and ensure that their personal information is not misused or abused. Some of the key laws and regulations include:
California Consumer Privacy Act (CCPA): The CCPA is a privacy law that applies to companies doing business in California and sets out rules for the collection, processing, and sharing of PII data.
Health Insurance Portability and Accountability Act (HIPAA): HIPAA is a US law that governs the handling of health information and sets out strict rules around the privacy and security of such data.
Children’s Online Privacy Protection Act (COPPA): COPPA is a US law that regulates the online collection and sharing of PII data from children under the age of 13.
General Data Protection Regulation (GDPR): The GDPR is a comprehensive data protection law that governs the handling of personal data by companies and organizations operating in the European Union (EU) or processing the data of EU citizens.
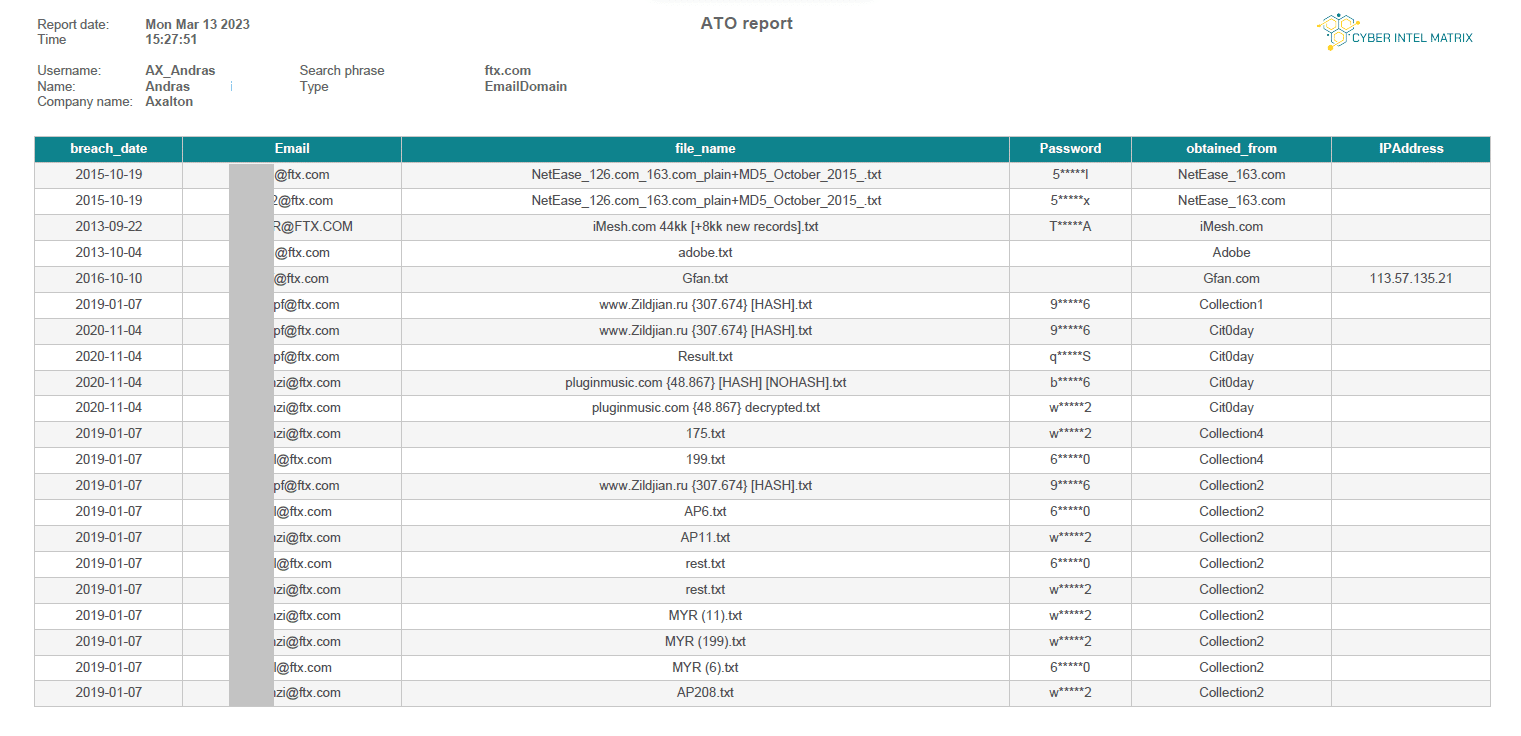
Screenshots
Benefits to End Users
Awareness
Being aware of a data breach and leaked credentials can help individuals and organizations take necessary steps to protect their sensitive data, including changing passwords, enabling two-factor authentication, and monitoring their accounts for suspicious activity.
Early detection
The CIM Account Takeover service provides early warning signs of a potential data breach, which can help end-users quickly detect and respond to any security threats.
Prevention
By providing information on the latest threats and vulnerabilities, CIM can help end-users take proactive measures to prevent a data breach from happening in the first place.
Education
CIM provides the evidence to support educational resources which help end-users understand the risks and consequences of data breaches and leaked credentials, as well as how to protect their data and stay safe online.
Peace of mind
By staying informed and taking necessary precautions, end-users can have peace of mind knowing that they are doing everything they can to protect their sensitive data.
Business model
SaaS Subscription
Customer’s analyst users receive access to CIM Account Takeover using an online interface. This enables analysts to create their own queries, gather information, and export pdf reports.
Subscription - Enriched feed (with API)
CIM can integrate its breached credentials ATO feed into customer’s platform, so queries can be run automatically and Credential Exposure Verification Reports generated for large databases of employees or clients.
CIM partners with cybersecurity companies, resellers of breached credential services
Credential Monitoring and IAM Solution Providers
Companies that offer preventive services related to breached credential databases typically specialize in identity and access management (IAM) solutions. IAM solutions aim to protect against unauthorized access to sensitive information and systems by ensuring that users are properly authenticated and authorized to access the resources they need.
Credential Monitoring and Threat Intelligence Providers
Companies that monitor the dark web and other online sources for compromised credentials and alert organizations when their credentials have been exposed. They may also provide intelligence on emerging threats and vulnerabilities related to credential breaches.
Identity and Access Management (IAM) Solution Providers
These companies provide solutions to help organizations manage access to their systems and data. They offer a range of tools and technologies to authenticate users, manage credentials, and control access based on specific policies.
Managed Security Service Providers (MSSPs)
MSSPs offer a range of cybersecurity services, including IAM solutions, threat intelligence, and incident response. They may also offer proactive monitoring and management of an organization’s security infrastructure to detect and prevent credential breaches before they occur.
Security Awareness Training Providers
They provide training and education to help employees understand the risks associated with credential breaches and how to avoid them. They may offer simulated phishing attacks, interactive training modules, and other tools to help employees become more aware of security threats.
Benefits to Resellers
CIM data feeds enhance the preventive services of cybersecurity companies related to breached credential databases so they can remain focused on helping organizations protect against unauthorized access and ensure that their sensitive data remains secure.
Opportunity for upselling
Resellers can leverage the information provided by CIM to offer additional security solutions or services to their clients, such as breach response and remediation services, or more advanced security solutions.
Improved customer retention
By proactively providing their clients with information about data breaches and leaked credentials, cybersecurity vendors can demonstrate their commitment to their clients’ security and build trust, which can improve customer retention rates.
Competitive advantage
Cybersecurity providers who are able to provide their clients with up-to-date information about data breaches and leaked credentials may be better positioned to compete with other service providers who do not offer these services.
Revenue growth
Offering breach and credential monitoring services to clients can generate new sources of revenue for resellers, as well as increase recurring revenue streams.
Better client relationships
By providing valuable information and services related to data breaches and leaked credentials, resellers can strengthen their relationships with their clients and become a trusted advisor for their security needs.
Target Markets
Large and small businesses
Companies that store sensitive customer and employee data are often targeted by cybercriminals. They need to know if their employees’ email addresses and passwords have been exposed in a data breach.
Technology companies
Tech companies that develop and sell software, hardware, and other technology products and services can also be targets of credential theft.
Financial institutions
Banks, credit unions, and other financial institutions have access to sensitive financial data. They need to know if their customers’ account information has been compromised. Financial services, such as banks, credit unions, and insurance companies, are a prime target for credential theft because they hold sensitive financial information.
Healthcare
The healthcare sector is also at high risk of credential theft, as electronic medical records and other sensitive patient data are highly valuable on the black market.
Government agencies
Government agencies hold sensitive information that is of interest to cybercriminals. Breached credentials can be used to gain unauthorized access to government systems and data. Government organizations hold sensitive information such as national security information, military information, diplomatic information and more.
Retail
Retailers are also at risk of credential theft, especially those that store customer data such as credit card information.
Education
Education sector holds a vast amount of sensitive data of both employees and students, including financial information, personally identifiable information, and educational records.
Individuals
Individuals who want to protect their personal online accounts and data from being compromised would also be interested in information about breached credentials.