CIM Dark Mapper
“Shodan” for the Dark Web.
Hacking the hackers.
Dark Mapper scans the Dark Web hidden services for network info, open ports, CMS (Content Management System) data, metadata, header information, and vulnerabilities. Unlike Shodan, this is mostly intel on Dark Web services, web servers, not connected devices, PLCs, or IoT.
This data does not exist anywhere else in the world.
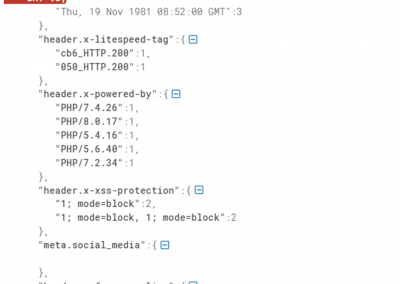
It includes vulnerabilities of Dark Web pages (WordPress and other CMS) users, open ports, CMS vulnerabilities, headers, as well as general info even from the content of these pages.
Dark Mapper provides lots of actionable information, also historical – for example investigators can see that an electrical components web shop used to be a weapons store just two weeks ago.
The service is provided as a feed into an existing SIEM, but manual searches using queries are also possible.

Features
Through Dark Mapper CIM cybersecurity experts provide valuable insights into threat actors and their tactics, techniques, and procedures (TTPs).
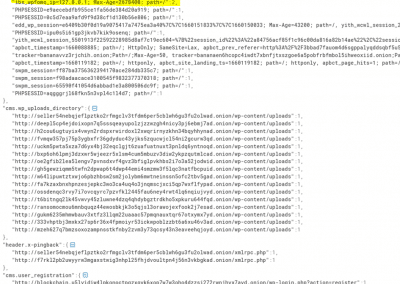
Dark Web hidden services & network info
The dark web is a hotbed for cybercriminal activity, and hidden services on the dark web can reveal valuable information about cyber threats. This includes details about the infrastructure that threat actors use to launch attacks, such as IP addresses, domain names, and network configurations.
Open ports & running services
Open ports are points of entry into a network that can be exploited by attackers. Knowing which ports are open and which services are running on them can help cybersecurity experts identify vulnerabilities and potential attack vectors.
Hacker CMS data
Many websites use content management systems (CMS) like WordPress or Drupal, which can be vulnerable to attacks if they are not properly secured. Attackers use exploits to target these systems, and understanding the specific CMS being targeted can help cybersecurity experts take proactive measures to mitigate risk.
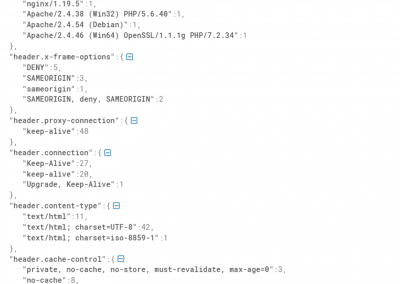
Metadata & header information
Metadata and header information can reveal details about the software, devices, and operating systems used by threat actors. This can help experts identify specific vulnerabilities and tailor their defenses accordingly.
Threat actor user info
Usernames and other identifying information can help cybersecurity experts track threat actors across different attacks and identify patterns in their behavior.
Operating systems & vulnerabilities
Knowing the operating system and software that threat actors use can help experts understand their capabilities and identify vulnerabilities that can be exploited.
Dark Web content
Dark web pages provide valuable intelligence on the tactics, techniques, and procedures used by threat actors. This includes information about malware, exploit kits, and other tools and techniques used to carry out attacks.
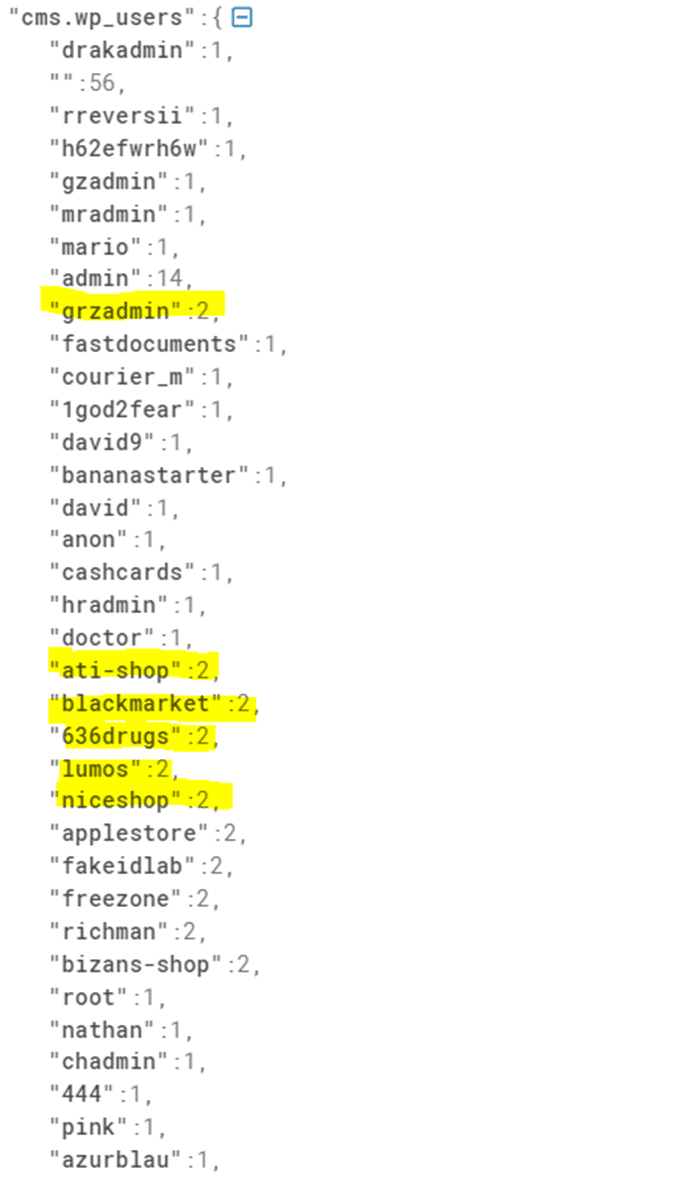
CIM Dark Mapper example of user names of WordPress webserver admins operating mostly illegal Dark Web web shops:
Extensive training and documentation available
Analyst services may be purchased alongside the platform
Screenshots of feed data
Benefits to LEA and SOC Operator End Users
Threat detection
CIM Dark Mapper provides SOC operators with valuable information on the tools and techniques that malicious actors are using to launch attacks. By monitoring the Dark Web for indicators of compromise (IOCs) associated with known tools and techniques, SOC operators can detect and respond to attacks more quickly.
Intelligence gathering
By identifying the weaknesses of a cyber attacker, law enforcement can gain valuable intelligence on the threat landscape. This intelligence can be used to inform law enforcement strategies and improve their overall ability to respond to cyber threats.
Disruption and prevention
If law enforcement is able to identify the weaknesses of a cyber attacker, they may be able to use that information to disrupt their operations and prevent future attacks. By targeting the weaknesses of the attacker, law enforcement can make it more difficult for them to operate and reduce the overall risk of successful attacks.
Investigation of Cybercrime
Law Enforcement Agencies (LEA) could use CIM’s information on the vulnerabilities of hackers’ systems to investigate cybercrime. By identifying and exploiting the weaknesses in a hacker’s infrastructure, LEA can gather evidence to help build a case against the hacker and potentially identify accomplices or other members of a criminal organization.
Preventing Cyber Attacks
LEA can use the information on hacker’s vulnerabilities to proactively identify and prevent cyber attacks. By sharing this information with other law enforcement agencies or with private sector organizations, LEA can help prevent future attacks, protect critical infrastructure, and reduce the potential damage caused by cyber threats.
Protecting National Security
LEA can use the information on hacker’s vulnerabilities to protect national security. By identifying and exploiting the weaknesses in the infrastructure of foreign adversaries or hostile actors, LEA can gather intelligence to help defend against cyber attacks and protect sensitive information.
Arrest and prosecution
If law enforcement is able to identify the weaknesses of a cyber attacker, they may be able to use that information to track and apprehend the individual or group responsible for the attack. Once the attacker is apprehended, law enforcement can use their weaknesses to build a case against them and secure a conviction in court.
Collaboration with industry partners
Law enforcement can work with industry partners to share information about cyber attackers’ weaknesses. This collaboration can help to build a more complete picture of the threat landscape and enable more effective defense strategies.
Business model
SaaS Subscription
Customer’s analyst users receive access to CIM Dark Mapper online. This enables analysts to create their own queries, gather information, and correlate data within the CIM Platform as well as with other third party sources.
SaaS Subscription with Analyst Services
CIM analysts do the heavy lifting for you. Customer’s analyst users explain the queries and context to CIM professionals, who gather information, correlate data, and publish reports.
Data feed (with API)
CIM can integrate its Dark Mapper feed into customer’s platform, so queries can be run automatically and reports on attacker infrastructure vulnerabilities can be generated.
CIM partners with vendors serving Law Enforcement and SOC Operators
Vendors of Hacker Vulnerabilities
The target market for CIM Dark Mapper is Law Enforcement Agencies (LEA), SOC operators, and cybersecurity companies providing Dark-Web-related services
Law Enforcement Agencies
CIM Dark Mapper reduces costs and enables LEA to close an investigation faster.
Security operations centers (SOCs)
SOC teams are responsible for monitoring and responding to security events in an organization. CIM Dark Mapper provides information on hackers’ IT infrastructure helping SOCs to detect and respond to attacks more quickly.
Incident response teams
Incident response teams are responsible for investigating security incidents and mitigating the impact of those incidents. CIM Dark Mapper helps incident response teams to quickly identify the source of an attack and take appropriate actions to contain and remediate it.
Threat intelligence teams
Threat intelligence teams are responsible for monitoring and analyzing cyber threats to an organization. CIM dark Mapper helps threat intelligence teams identify emerging threats and vulnerabilities and take proactive measures to mitigate them.
Benefits to Vendors
Higher revenues and profits
Resellers can earn a profit by selling information on hackers to law enforcement agencies and SOC operators. The information can be valuable to these organizations, and they may be willing to pay a premium for it.
Reputation and credibility
By providing valuable information to law enforcement agencies and SOC operators, resellers can establish themselves as experts in the field of cybersecurity. This can enhance their reputation and credibility within the industry, which can lead to additional business opportunities.
Access to additional customers
By working with law enforcement agencies and SOC operators, resellers can gain access to additional customers who may be interested in their other products and services. This can help to expand their customer base and increase their revenue.
Contribution to the fight against cybercrime
Resellers who sell information on hackers to law enforcement agencies and SOC operators can also contribute to the fight against cybercrime. By providing valuable intelligence, they can help these organizations to better understand the threat landscape and develop more effective defense strategies.