CIM Exposure Report
The CIM Exposure Report is a one-time cybersecurity maturity assessment report, a snapshot in time, identifying compliance failures, detecting weak points in the corporate and supplier networks, in production systems and industrial facilities as well as in overall data integrity.
The CIM Exposure Report provides a standard vulnerability score card, so businesses can compare results to their competitors or themselves over time. The transparent scoring system attaches actual man hours and a dollar value to remediation, potential financial loss, based on CVSS and the annual IBM Security Cost of a Data Breach Report, not counting for any potential fallout from lawsuits or downtime in case of a breach.
The CIM Exposure Test is a continuous subscription-based automatic assessment of a person’s or a company’s current and historical exposure in the Dark Web, revealing stolen credentials and sensitive information which may be used in social engineering campaigns. CIM Exposure Test is designed to help businesses identify potential breaches in their network in real time.

Features
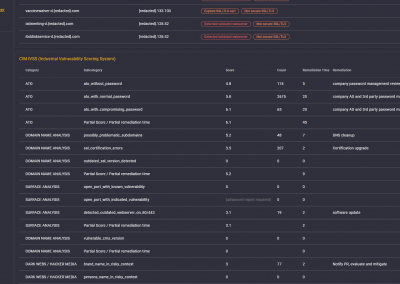
Both the CIM Exposure Report and the CIM Exposure Test uses the CIM IVSS (Industrial Vulnerability Scoring System) which examines the following areas for vulnerabilities, among others:
Breached credentials (Account Takeover, ATO)
ATO without password
ATO with normal password
ATO with compromising password
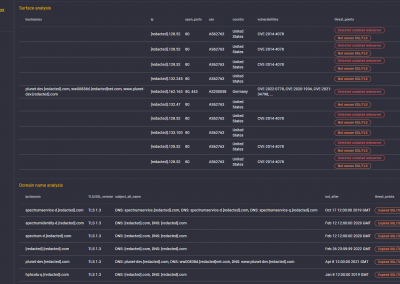
Domain name analysis
Possibly problematic subdomain
SSL certification errors
Outdated SSL version
Surface analysis
Open ports with known vulnerability
Open ports with indicated vulnerability
Detected outdated HTTP Webserver on p 80/443
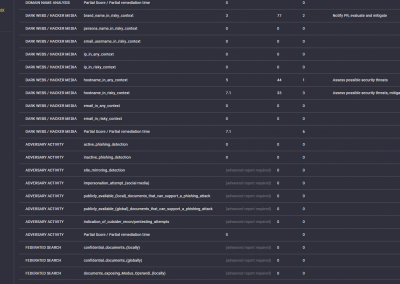
Exposure on the Dark Web / Pastebins / Hacking forums
Brand name in risky context
Person’s name in risky context
Email-Username in risky context
IP in any context
IP in risky context
Hostname in any context
Hostname in risky context
Email in any context
Email in risky context
Adversary activity
Phishing detection
Site mirroring detection
Impersonation attempt (social media)
Publicly available (local) documents that can support a phishing attack
Publicly available (global) documents that can support a phishing attack
Indication of outsider recon/pentesting attempts
Federated search evaluation
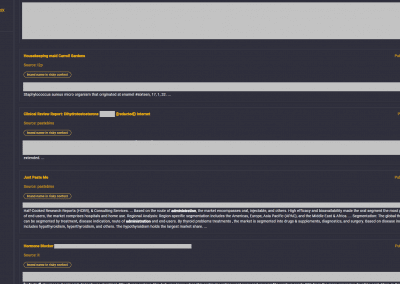
Confidential documents (locally & globally)
Documents exposing Modus Operandi (locally & globally)
Documents with default credentials on Phys/LAN (locally & globally)
Documents with default credentials of company login (locally & globally)
Technical Documents exposing Network/Industrial Infrastructure (locally & globally)
Documents with compromising personnel information (globally)
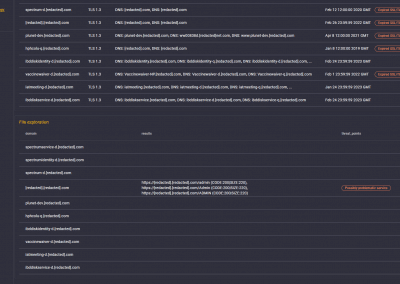
File exploration
Backup/Documents with confidential data
Backup/Documents exposing Modus Operandi
Backup/Documents with credentials on Phys/LAN
Backup/Documents with credentials on Internet
Backup/Documents with personnel data
Unsecured submit interface
Operational Technology risk assessment
Industrial device / sensor / IoT / PLC detection
Industrial device / sensor / IoT / PLC with nologin web access
Low or medium vulnerability of the supply chain
Critical vulnerability of the supply chain
CIM Exposure Test
The CIM Exposure Test, the subscription-based automatic Customer Privacy Exposure Check, consists of the following sections:
CIM Credential Exposure Test
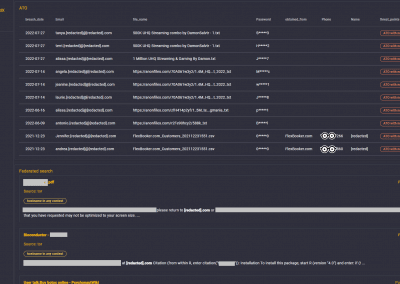
The Credential Exposure Test tests for the exposure of user credentials, such as usernames and passwords, on the internet. It scans public data repositories and forums to check if any of the company’s credentials have been leaked or exposed. The Credential Exposure Test also checks for weak passwords and password reuse, which can lead to a breach.
CIM Port Exposure Test
The Port Exposure Test tests for open ports on the company’s network. Open ports can be used by attackers to gain access to a network, and can indicate potential vulnerabilities that need to be addressed. The CIM Port Exposure Test checks for open ports on both internal and external networks.
CIM IP Exposure Test
The IP Exposure Test tests for IP address exposure. It scans the internet for any IP addresses associated with the company, and checks if any of them have been blacklisted or are associated with malicious activity. The CIM IP Exposure Test also checks for open ports and services on each IP address.
CIM Domain Exposure Test
The Domain Exposure Test tests for domain exposure. It checks if any of the company’s domains have been blacklisted or are associated with malicious activity. The CIM Domain Exposure Test also checks for subdomains and email addresses associated with each domain.
CIM File Exposure Test
The File Exposure Test tests for file exposure. It scans the internet for any files associated with the company, and checks if any of them contain sensitive information or have been exposed publicly. The CIM File Exposure Test also checks for files with weak permissions, which can lead to unauthorized access.
CIM Dark Web Exposure Test
The Dark Web Exposure Test tests for exposure on the dark web. It scans dark web marketplaces and forums for any mention of the company or its employees. The CIM Dark Web Exposure Test also checks for leaked data and credentials on the dark web.
CIM Federated Exposure Test
The Federated Exposure Test tests for exposure through third-party services. It checks if any third-party services the company uses have been compromised or have exposed the company’s data. The CIM Federated Exposure Test also checks for any potential vulnerabilities in the company’s integrations with third-party services.
Extensive training and documentation available
Analyst services may be purchased alongside the platform
Modular pricing - Each module may be ordered separately
Screenshots
Benefits to Customers
The CIM Exposure Report and Exposure Test services provide several benefits for their target market, which are clients and companies that want to assess and improve their cybersecurity posture.
Improved Cybersecurity Maturity
The CIM Exposure Report provides a snapshot of a company’s current cybersecurity posture, identifying compliance failures and weak points in their network. By identifying these vulnerabilities, companies can take steps to improve their cybersecurity and reduce the risk of a data breach or other cyber attack.
Financial Risk Assessment
The report attaches actual man-hours and a dollar value to remediation and potential financial loss based on the most widely accepted cyber-industry standard CVSS (Common Vulnerability Scoring System) and the annual IBM Security Cost of a Data Breach Report. This allows companies to understand the financial risk associated with their cybersecurity posture and make informed decisions about where to allocate resources for remediation.
Standardized Comparison
The report provides a standard vulnerability score card that allows businesses to compare their cybersecurity posture to their competitors or themselves over time. This provides a benchmark for improvement and helps companies prioritize remediation efforts.
Real-Time Monitoring
The CIM Exposure Test service provides continuous subscription-based automatic assessment of a company’s exposure in the Dark Web. This helps businesses identify potential breaches in their network in real-time, allowing for quick remediation and minimizing the damage from a cyber attack.
Benefits to End Users, Employees, Clients
The benefits to end user consumers of the CIM Exposure Report and Exposure Test is indirect, as these services are primarily designed for businesses to assess and improve their cybersecurity posture. However, end users may benefit from the increased security and protection of their personal data that can result from businesses using these services to identify and remediate vulnerabilities in their networks. Additionally, the transparent scoring system and benchmarking against competitors may provide greater accountability and motivation for businesses to prioritize cybersecurity and protect the data of their customers and clients. In the case of the CIM Exposure Test, end users may benefit from the real-time monitoring and identification of potential breaches, which can help to prevent the unauthorized use of their personal information.
Business model
CIM Exposure Report and Exposure Test provide businesses with a holistic view of their potential vulnerabilities and help them take steps to protect their data and networks.
The standard service is provided as an automated passive network & supplier vulnerability scoring report.
There are also advanced, tailored services for compromised data assessment and compromised customer and/or employee credential check, however these require more configuration and possible development, (These services would almost qualify as penetration testing) which we are happy to do.
CIM Exposure Report
CIM Exposure Report delivered as a pdf file or credentials are provided for online access
Subscription-based ongoing CIM Exposure Test
CIM Exposure Test requires a subscription to the service, providing continuous monitoring
CIM partners with distributors, vendors of exposure and vulnerability reports
Exposure Test Vendors
Resellers of cybersecurity exposure tests and vulnerability reports are typically companies that specialize in providing cybersecurity services or products. They resell these reports to help their clients identify and mitigate security risks and to provide a more comprehensive cybersecurity solution. It also gives them an opportunity to sell their solutions as an answer to specific — exposed — customer problems.
Cybersecurity consulting firms
Cybersecurity consulting firms provide a range of services, including vulnerability assessments and penetration testing. They may resell cybersecurity reports as part of their broader cybersecurity consulting services.
Managed Security Service Providers
MSSPs offer managed security services, such as security monitoring, threat detection, and incident response. They may resell cybersecurity reports to their clients to help identify and mitigate security risks.
Value-added resellers (VARs)
VARs resell hardware, software, and other technology products, often with additional services such as installation and maintenance. They may resell cybersecurity reports as part of their overall security offering.
Independent software vendors (ISVs)
ISVs develop and sell software applications, including cybersecurity software. They may resell cybersecurity reports to their customers as part of their software offering.
Cybersecurity product vendors
Companies that develop and sell cybersecurity products, such as firewalls, intrusion detection systems, and antivirus software, also resell cybersecurity reports to complement their product offerings.
Benefits to Exposure Test Vendors
Additional Revenue Stream
Resellers can generate additional revenue by selling the CIM Exposure Report and Exposure Test services to their existing customer base or new prospects. As cybersecurity is a growing concern for many businesses, there is a significant demand for these services.
Increased Customer Retention
By offering cybersecurity exposure report services, resellers can provide their customers with additional value and help them mitigate the risk of cyber attacks. This can increase customer satisfaction and retention rates.
Competitive advantage
By offering CIM’s cybersecurity exposure test services, resellers can differentiate themselves from competitors who may not offer these services. This can help them win new business and retain existing customers.
Sales and Marketing Support
CIM provides resellers with sales and marketing support, such as training, collateral, and lead generation programs. This can help resellers effectively sell and promote these services to their customers.
Target Markets
Large corporations
Large corporations with complex IT infrastructure and sensitive data are often a prime target for cyberattacks. These companies may purchase cybersecurity exposure and vulnerability reports to identify and mitigate any security risks in their systems.
Financial institutions
Banks, insurance companies, and other financial institutions hold sensitive customer data and are often targeted by cybercriminals. These companies may purchase cybersecurity reports to assess the security of their systems and ensure compliance with regulatory requirements.
Healthcare providers
Healthcare providers store sensitive patient information, making them a prime target for cyberattacks. These companies may purchase cybersecurity reports to identify vulnerabilities in their systems and implement appropriate security measures to protect patient data.
Retail companies
Retailers often collect sensitive customer information such as payment card data, personally identifiable information, and purchasing history, making them a potential target for cyberattacks.
Retail companies also need to comply with data protection regulations, such as the Payment Card Industry Data Security Standard (PCI DSS), which requires regular vulnerability assessments and penetration testing to maintain compliance.
In addition to protecting customer data, exposure reports can also help retail companies maintain their brand reputation and avoid costly data breaches. A successful cyberattack can damage a company’s reputation and lead to significant financial losses, making it essential for retailers to prioritize cybersecurity.
Government agencies
Government agencies hold sensitive information related to national security, defense, and other critical functions. These agencies may purchase cybersecurity reports to ensure the security of their systems and data.
Small and medium-sized enterprises (SMEs)
SMEs may purchase cybersecurity exposure reports to assess the security of their systems and mitigate any potential risks. This is particularly important as cyberattacks against smaller companies have been on the rise in recent years.