CIM Framework Platform
CIM Framework Platform is the flagship product of Cyber Intel Matrix. A dashboard enables analysts and investigators to perform manual searches, using specialized queries, in intel databases as well as industrial honeynet databases.
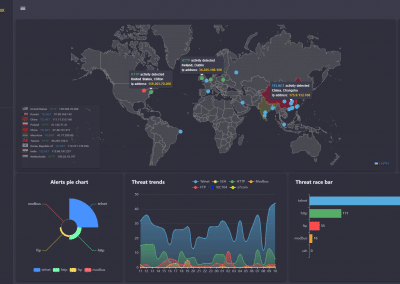
The platform monitors and detects attacks on ICS protocols and industrial honeynet devices and combines several IT threat feeds, interactive security tools, as well as continuously expanding intelligence databases to enrich data: Dark Web (TOR, I2P), Pastebin sites, Hacking forums, Discord/Telegram groups, Malware Lab, APT Groups. The platform enables asset and username search, correlates data from numerous OSINT databases and vulnerability repositories (CVE) with its proprietary sources.

Features
Areas of Competence
Industry specific honeypot IoC alerts
Data searched and procured by CIM includes identities, threat actors, malicious hosts, IP address, geolocation, ports, indicators, attack patterns, malware, tools, locations, vulnerabilities, and intrusion sets.
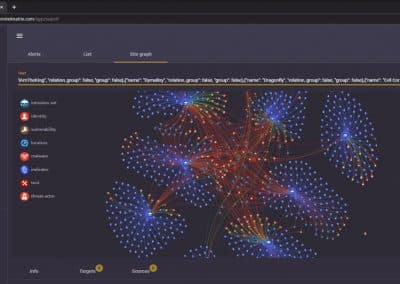
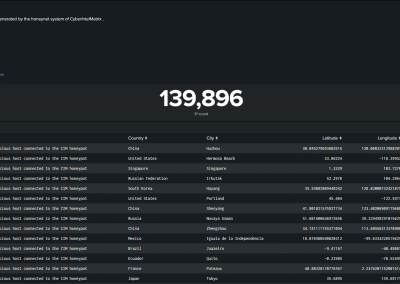
All CIM honeypot data gathered in its proprietary industrial cyber deception network called CIM Blackpot Honeynet is mapped to the STIX/TAXII standard, communicated in JSON object notation, as well as MISP.
As approved standards, Structured Threat Information Expression (STIX) and Trusted Automated Exchange of Intelligence Information (TAXII) are widely used to prevent and defend against cyberattacks by enabling threat intelligence to be analyzed and shared among trusted partners and communities. The STIX standard defines a JSON-based language for sharing structured threat intelligence in a consistent, machine-readable manner.
MISP is the leading Open Source Threat Intelligence and Sharing Platform (formerly known as the Malware Information Sharing Platform), used among others by NATO.
Intel queries
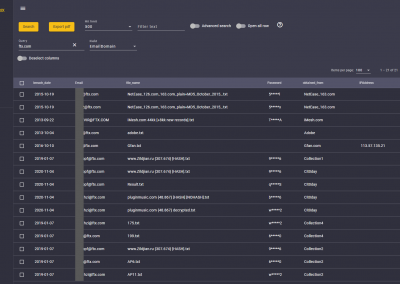
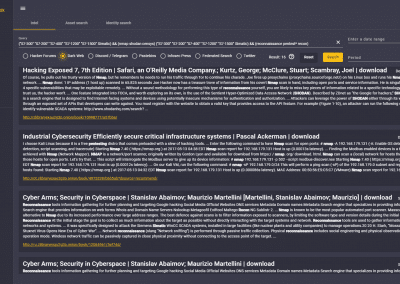
Wide-Range Intelligence Database: OSINT (Open Source Intelligence) database of leaked data and compromised corporate datasets, much more than leaked passwords and data privacy. Available as a separate service, click here. Focus on the fintech and healthcare sectors. Due to the nature of the data, it is impossible to annotate, so it is provided in the form of raw feeds.
Simple or complex search queries can be placed to search the following databases: hacker forums, Dark Web, Discord and Telegram communication channels, pastebin sites, data repositories, and generally the infosec press, Github, Bitbucket, and Twitter, among others.
ATO (Account Takeover) breached credentials database
Account Takeover (ATO) is CIM’s Breached Credentials Database. Available as a separate service, click here. Real-time verification against an annotated 20+ billion breached credentials database (user names, passwords, phone numbers, addresses, IP numbers, email addresses) as part of the CIM Framework. Reveals leaked credentials in real time and other valuable PII used for social engineering.
- All record fields searchable
- Passwords intentionally masked
- Advanced search & query options
- Historical data going back 12+ years
Malware Lab
Passive malware analysis, can extract IP addresses, uses YARA rules, signatures recognized across a continually updated shared repository, provides Virustotal enrichment.
User can upload new files for analysis.
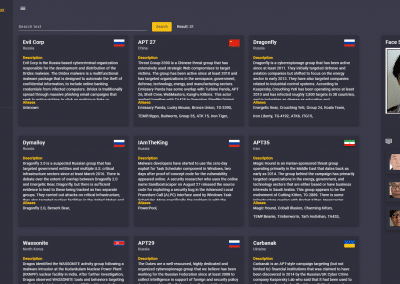
Advanced Persistent Threat (APT) Groups
Attacker IoCs can be correlated to each other, known groups, attacks and malware after searches on the Dark Web.
Includes a face recognition module which can be connected to law enforcement or Internet databases, to build a database of known threat actors.
May be integrated into SIEM platforms
CIM has developed a proprietary app (integarted with IBM QRadar or Splunk), providing much more than a feed. It is more interactive, alerts may be queried with a right-click, no need to copy-paste user names, file hashes, IP addresses. Analysts can check whether data appears in the CIM database, thus validating attacker addresses, for example. We have also created extensions within the SIEM to open CIM search windows to perform manual searches and download data in CSV format. (See below for screenshots)
Common CIM feeds to integrate:
- CIM TOR exit nodes
- CIM honeypot alerts
- CIM malware hashes
- CIM attacker IP addresses of activity logged in the CIM Blackpot Honeynet


Extensive training and documentation available
Analyst services may be purchased alongside the platform
Screenshots
Benefits to End Users
Proactive threat detection
CIM CTI services help organizations identify potential cyber threats before they cause damage or disruption.
Better situational awareness
The CIM Framework Platform provides organizations with a better understanding of the cyber threat landscape and the potential risks facing their systems and data.
Improved incident response
CIM CTI services help organizations respond more quickly and effectively to cyber incidents by providing timely and accurate information about the threat.
Compliance support
CIM services help organizations meet regulatory requirements for cybersecurity by providing actionable intelligence about emerging threats and vulnerabilities.
Enhanced threat intelligence sharing
The CIM Threat Intelligence Platform enables companies to share threat intelligence data with trusted partners and other organizations to help improve overall cyber defenses.
Prioritization of cybersecurity resources
CIM helps organizations prioritize their cybersecurity resources by focusing on the most significant and relevant threats.
Reduction in false positives
CIM CTI feeds help reduce false positives by providing context and additional information about potential threats.
Business model
SaaS Subscription
Customer’s analyst users receive access to the various services of the CIM Framework Platform online. This enables analysts to create their own queries, gather information, and correlate data within the CIM Platform as well as with other third party sources.
SaaS Subscription with Analyst Services
CIM analysts do the heavy lifting for you. Customer’s analyst users explain the queries and context to CIM professionals, who gather information, correlate data, and publish reports.
CIM partners with distributors, vendors of threat intelligence services
CTI Vendors
Cyber threat intelligence (CTI) is a specialized type of threat intelligence that focuses on identifying and analyzing cyber threats. CIM’s Enriched CTI feeds and CTI as a Service can be used by a variety of companies that specialize in cybersecurity, intelligence, or data analysis, to enhance their services.
Cybersecurity Vendors
Many cybersecurity vendors offer CIM CTI services as part of their broader suite of cybersecurity solutions.
Threat Intelligence Providers
Specialized threat intelligence providers focus specifically on collecting and analyzing threat intelligence data.
Managed Security Service Providers
Managed security service providers (MSSPs) offer CIM CTI services as part of their broader managed security services.
Technology Companies
Technology companies offer CIM CTI services as part of their broader portfolio of software and services.
Benefits to CTI Vendors
Higher revenues and profits
Higher quality (and quantity) of service
While lowering false positives
Enhanced accuracy and coverage
Having CIM’s extensive CTI databases and analyst services can help CTI vendors improve the accuracy and coverage of their threat intelligence by providing more data points and expert analysis.
Improved threat detection and response
With access to CIM’s larger and more comprehensive database of threat intelligence, CTI vendors can better detect and respond to emerging threats, allowing them to provide more effective protection to their customers.
Competitive advantage
By having a larger and more comprehensive database of threat intelligence and expert analysis, CTI vendors can differentiate themselves from their competitors and offer more valuable services to their customers.
Improved efficiency
Using the CIM Platform or threat intel feeds, CTI vendors can save time and resources by leveraging existing data and analysis, rather than conducting their own research from scratch.
Customization and personalization
CTI vendors can offer more customized and personalized services to their customers, tailored to their specific needs and risk profile.
Increased customer satisfaction
By providing more accurate and effective threat intelligence and analysis, CTI vendors can improve customer satisfaction and retention, leading to long-term business growth and success.
Target Markets
Threat Intelligence
Enterprise
Large organizations with complex IT infrastructures are the primary market for Threat Intelligence Platforms (TIPs). These organizations require advanced threat intelligence capabilities to protect against sophisticated cyber attacks and to ensure compliance with regulatory requirements.
Government
Federal and state governments, as well as local law enforcement agencies, use TIPs to protect national security interests, critical infrastructure, and sensitive data.
Financial services
The financial industry is a prime target for cyber attacks, and TIPs like CIM are used to help detect and prevent fraud, money laundering, and other financial crimes.
Healthcare
The healthcare industry is another prime target for cyber attacks due to the large amount of sensitive data stored in electronic health records. The CIM TIP is used to help protect against data breaches and other cyber threats.
Education
Schools and universities are increasingly being targeted by cyber criminals, and TIPs are used to help protect student data and academic research.
Technology
Technology companies are prime targets for cyber attacks, and TIPs are used to help protect intellectual property and sensitive data.
Industrial Threat Intelligence
Energy
Oil and gas companies, electric utilities, and other energy companies are highly reliant on industrial control systems (ICS) to operate critical infrastructure. The CIM Industrial Threat Intelligence Platform (ITIP) helps protect these systems against cyber attacks that could cause physical damage or disrupt operations.
Manufacturing
Manufacturers rely heavily on automated processes and robotics, which can be vulnerable to cyber attacks. ITIPs can help detect and prevent cyber threats that could disrupt production or compromise sensitive intellectual property.
Transportation
Transportation systems, such as railways and airports, are increasingly connected to the internet and vulnerable to cyber attacks. The CIM ITIP helps protect these systems against cyber threats that could disrupt operations or compromise safety.
Chemicals
Chemical companies often handle dangerous substances and are required to comply with strict safety regulations. CIM ITIP can help protect against cyber threats that could cause physical harm or disrupt compliance efforts.
Defense
Military organizations are highly reliant on industrial systems, and cyber attacks against these systems could have serious national security implications. CIM can help protect against cyber threats that could compromise defense capabilities or sensitive information.