CIM Intel Database
The CIM Intel Database service is part of the CIM Framework Platform, but is also offered separately. Wide-Range Intelligence Database: OSINT (Open Source Intelligence) database of leaked data and compromised corporate datasets, much more than leaked passwords and data privacy. Focus on the fintech and healthcare sectors. Due to the nature of the data, it is not annotated, it is provided in the form of raw feeds. CIM sources and indexes (refers to) the data, making it possible for authorized customers to obtain it directly.

Features
Areas of Competence
Queries
Simple or complex search queries can be placed to search the following databases: hacker forums, Dark Web, Discord and Telegram communication channels, pastebin sites, data repositories, and generally the infosec press, Github, Bitbucket, and Twitter, among others. The service is easy to use using Google-type queries.
Hacker Forums
Hacker forums are online platforms where hackers, cybersecurity experts, and enthusiasts exchange information, tools, and techniques related to hacking and cybersecurity.
These forums are often hidden or obscured from search engines and require membership to access. The discussions on these forums may range from tutorials on exploiting vulnerabilities to discussions of new malware or tools that can be used in cyber attacks.
Hacker forums can be both a boon and a bane to the cybersecurity community. While they can provide a platform for security professionals to learn about new vulnerabilities and emerging threats, they can also be used to facilitate cybercrime and illegal activities. Additionally, some forums may be used to recruit new hackers or facilitate the sale of stolen data or illicit software.
It is important for cybersecurity professionals to monitor these forums and keep up-to-date with the latest trends and techniques used by hackers to better protect their organization or clients from cyber attacks. Additionally, it is essential to report any suspicious activities or content to the appropriate authorities to help prevent cybercrime.
Some examples of typical known hacker forums:
- Hack Forums: This is one of the most well-known hacker forums, with over a million registered users. It has a reputation for being a hub for cybercriminals, with discussions on hacking, cracking, and other illegal activities.
- RaidForums: This was another popular hacker forum that has gained notoriety for hosting databases of stolen data, such as login credentials and credit card information. Closed down, became Breached.vc which in turn was also locked down. (Note CIM has successfully located its previous content, making it available to customers in its historical archives)
- Nulled: This is a forum that specializes in sharing pirated software and other digital content, as well as providing tutorials and resources for hacking and cracking.
- Dark0de: This was a notorious hacker forum that was shut down by law enforcement in 2015. It was known for hosting discussions and trading of malware, as well as offering hacking services for hire.
- Hell: This is a Russian-language hacker forum that has gained a reputation for being a hub for cybercriminals operating in Eastern Europe. It offers a variety of hacking tools and services for sale, as well as discussion forums on various illegal activities.
It is important to note that accessing or participating in these forums is illegal in most countries and can result in serious consequences, including fines and imprisonment. CIM strongly advises against accessing these forums or engaging in any illegal activities.
Dark Web
The dark web is a subset of the internet that is not indexed by search engines and is only accessible through special software, such as the Tor browser.
The dark web is made up of a collection of networks, the most well-known of which is the Tor network. Tor stands for “The Onion Router,” which refers to the way data is encrypted and routed through multiple layers, or “nodes,” before it reaches its final destination. This makes it difficult for anyone to trace the path of the data and identify the source or destination.
Other dark web networks include I2P (Invisible Internet Project), which is similar to Tor but focuses on peer-to-peer file sharing, and Freenet, which is designed for anonymous publishing and file sharing.
The dark web is often associated with illegal activities, such as drug sales, weapons trading, and hacking services. It is also a haven for cybercriminals, who use it to buy and sell stolen data, such as credit card information, personal identities, and even access to compromised computers.
The anonymity provided by the dark web makes it difficult for law enforcement agencies to track down cybercriminals, which is why it is often used by hackers, scammers, and other malicious actors.
It is important to note that not everything on the dark web is illegal, and it can be used for legitimate purposes, such as anonymous communication and whistleblowing. However, the risks of using the dark web are high, as users are exposed to malware, scams, and other security threats.
CIM cybersecurity professionals advise against accessing the dark web unless it is absolutely necessary, and only after taking appropriate security measures, such as using a secure VPN and other anonymity tools.
Discord/Telegram
Discord and Telegram are messaging platforms that allow users to create channels or groups for communication with others. Discord is primarily used for gaming communities, while Telegram is used for general communication and message broadcasting.
In the cybersecurity scene, Discord and Telegram channels are often used by both cybercriminals and cybersecurity professionals. Cybercriminals use these platforms to exchange information on new vulnerabilities, sell or trade stolen data, and plan and coordinate attacks. They may also use these platforms to recruit new members to their criminal enterprises.
On the other hand, cybersecurity professionals use Discord and Telegram channels to share information on the latest threats and vulnerabilities, discuss security best practices, and collaborate on projects. There are also many public channels that share news and updates related to cybersecurity.
Discord and Telegram channels can play a role in both facilitating and preventing cybercrime. For cybercriminals, these channels provide a means of communication that is difficult to monitor or trace.
Pastebins
Pastebin sites are online platforms that allow users to store and share text data, such as code snippets, logs, and notes. These sites are often used by developers, researchers, and other individuals to share information or collaborate on projects.
However, Pastebin sites are also commonly used by cybercriminals to share stolen data, such as login credentials, credit card numbers, and other sensitive information. They can be used to host code for malware, as well as to post ransom notes or threats.
Pastebin sites are often preferred by cybercriminals because they provide a means of sharing information that is difficult to trace or monitor. Many Pastebin sites allow users to remain anonymous, and the content can be deleted after a specified time.
CIM cybersecurity professionals actively monitor Pastebin sites for any information related to security threats or data breaches. Many cybersecurity researchers use Pastebin to gather information on emerging threats, and some security tools are available, for example CIM Intel Database, that can automatically monitor and analyze data posted to these sites.
Infosec Press
Infosec press refers to the various media outlets and publications that cover topics related to information security, such as data breaches, malware, cyber attacks, and other security threats.
These publications range from specialized news sites and blogs to traditional media outlets, such as newspapers and TV networks, that have dedicated technology and cybersecurity sections. Some examples of popular infosec publications include Dark Reading, KrebsOnSecurity, Threatpost, and SecurityWeek.
Infosec press is important for cybersecurity professionals because it provides them with the latest news and insights into the evolving cybersecurity landscape. By staying up-to-date with the latest security threats and trends, professionals can better understand the risks facing their organization and develop effective strategies to mitigate them.
Infosec press can also help professionals stay informed about new tools, technologies, and best practices in the field of cybersecurity. This can be especially important for individuals who are responsible for securing their organization’s systems and data.
Federated Search
Aggregated results of meta search engines. Enables focused search on an entity or topic where the most relevant results are displayed, including corporate websites, Wikipedia, LinkedIn, Glassdoor, certain social media platforms and search engines like Google, Yahoo, Yandex, Bing, as well as news outlets, Github, Reddit, Bitbucket, etc. to conduct extensive analysis and investigation. This is especially relevant if the issue involves a security breach, data leak, or other potential cyber threats.
Federated Search can be used to look for IP addresses, emails, proxies, combo lists, among others.
GitHub and Bitbucket are web-based hosting services that allow developers to store, manage, and collaborate on their source code and software projects. These platforms are relevant from a cybersecurity point of view because they can be used to identify potential security risks and vulnerabilities in the code.
GitHub and Bitbucket allow developers to share their code with others and work collaboratively on projects. This can be beneficial in terms of improving the quality and security of the code, as multiple developers can review and test the code to identify potential issues. However, it also means that any security vulnerabilities in the code can be easily accessed and exploited by attackers.
From a cybersecurity perspective, it is important to ensure that the code hosted on these platforms is secure and free from vulnerabilities that could be exploited by attackers. This includes conducting regular code reviews and testing to identify and fix potential security issues.
By conducting an extensive analysis and investigation of the entity or topic in question, companies can gather valuable information that can help them identify potential vulnerabilities, assess the risk level of the issue, and develop a targeted response plan.
The use of the various sources in the CIM Intel Database and other relevant online platforms, can provide a comprehensive view of the entity or topic, including its history, reputation, and potential associations with other entities or individuals.
For example, if a company suspects that an employee may be involved in a data leak, a focused search on the employee’s name may reveal any online activity, such as GitHub or Bitbucket accounts, that could be relevant to the investigation. Similarly, a search on a specific topic, such as a new technology being developed by a competitor, could reveal any potential security risks associated with the technology or its developers.
CIM uncovers valuable information quickly that can be used to better understand potential security risks and develop effective strategies to mitigate them. It is important to conduct these searches in a legal and ethical manner, respecting the privacy and rights of all individuals and entities involved.
Real-time cybersecurity-related information that may be relevant from the microblogging site.
Firstly, Twitter is used as a source of information for security professionals to stay up-to-date with the latest security threats, vulnerabilities, and trends. Many cybersecurity experts, researchers, and organizations have a presence on Twitter, and regularly share news, insights, and analysis related to the cybersecurity landscape.
Twitter is also used to disseminate information about security incidents and respond to potential security threats. For example, organizations use Twitter to notify their customers and followers about a security breach or data leak, and provide updates on the response efforts and mitigation strategies.
In addition, Twitter is used for threat intelligence and analysis. Cybersecurity professionals at CIM monitor Twitter activity to identify potential security risks, such as phishing scams or malware campaigns, and take appropriate action to mitigate them.
Another important aspect of Twitter from a cybersecurity perspective is incident response. In the event of a security incident, Twitter is used to communicate with customers, stakeholders, and other parties involved, providing real-time updates and answering questions.
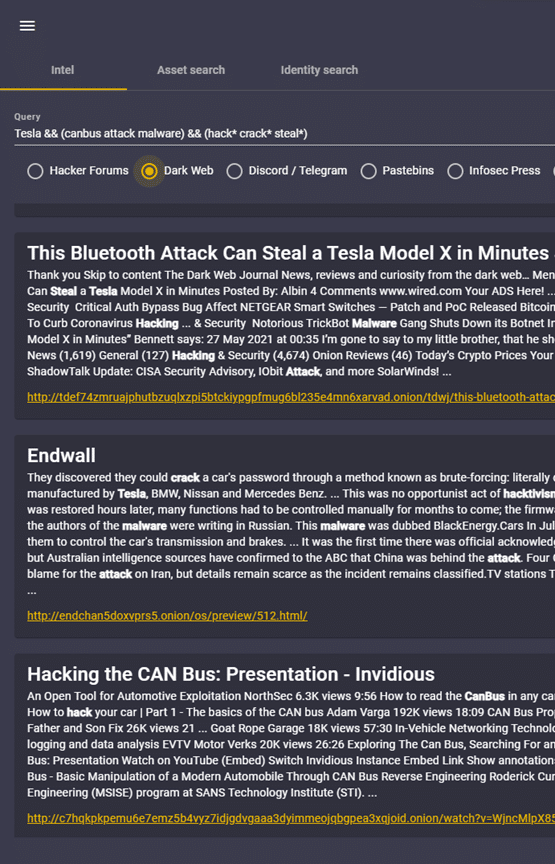
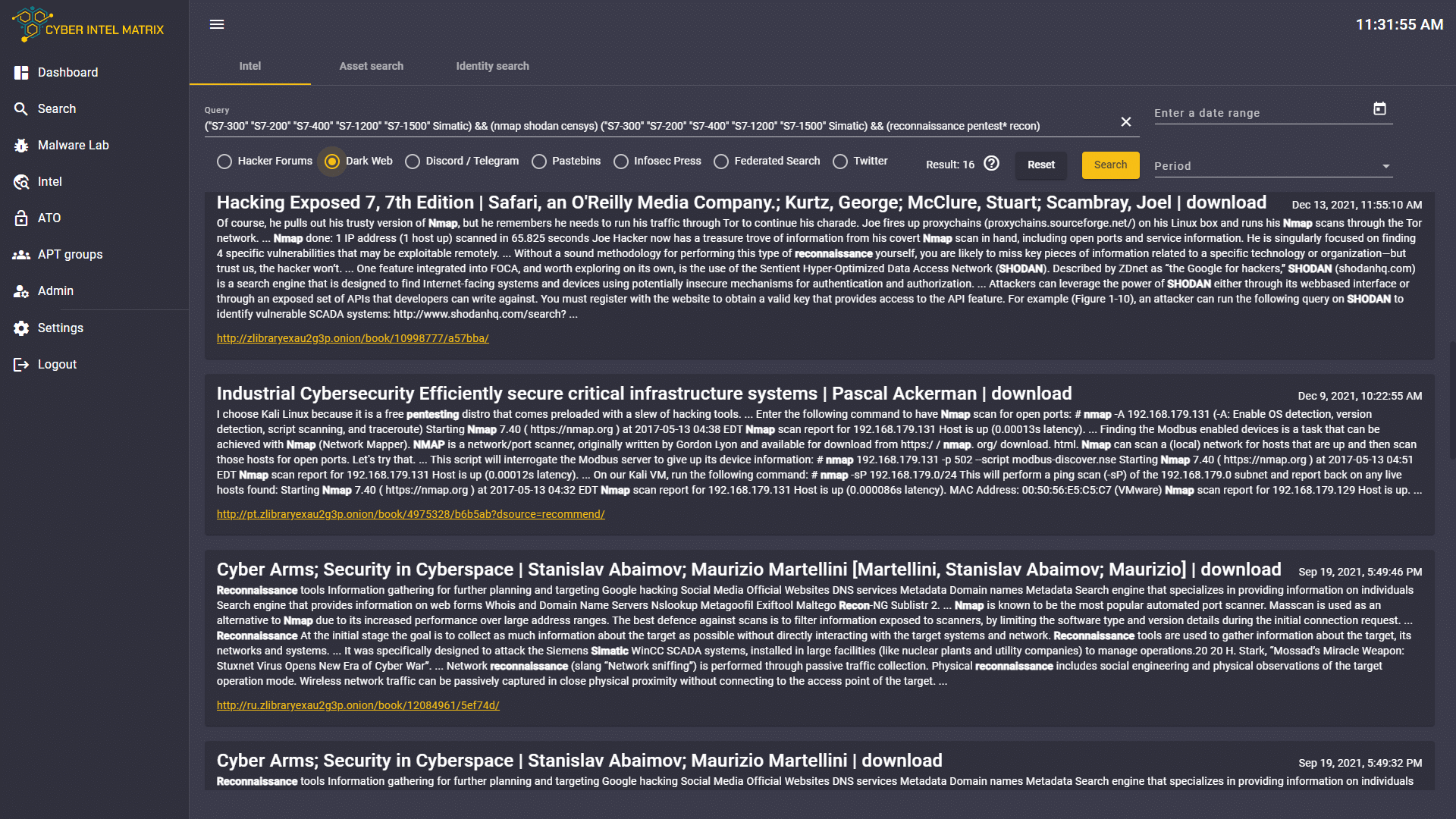
Example of CIM Intel Database at work
A search query using logical operators and wildcards was used to find detailed results.
Other examples include parking data, VIN numbers and license plates, so threat actors can determine where someone parked their car on September 11th, for example.
Another published information trove is the 2021 Facebook leak of 500 million users’ data, which does not contain passwords, so it is not considered a credential breach, but contains all other relevant PII information.
Extensive training and documentation available
Analyst services may be purchased alongside the platform
Historical data of banned and shut-down sources available
Dark Web pages often disappear after a few months uptime.
Screenshot
Benefits to Customers
Cybersecurity companies
CIM Intel Database can help cybersecurity companies identify potential security threats and vulnerabilities that their clients may face. This can enable them to provide more comprehensive and effective threat intelligence, incident response, and penetration testing services to their clients.
Law enforcement agencies
CIM Intel Database can provide valuable information to law enforcement agencies investigating cybercrime. This information can include data on potential suspects, online criminal activities, and emerging threats, which can help law enforcement agencies identify and apprehend cybercriminals.
Corporate security teams
CIM Intel Database can help corporate security teams monitor for potential threats and vulnerabilities to their organization’s systems and data. This can enable them to take proactive measures to mitigate these risks, such as strengthening their security controls and implementing security awareness training for employees.
Risk management teams
CIM Intel Database can help risk management teams assess the level of risk associated with a particular entity or dataset. This can enable them to make informed decisions related to risk mitigation and to implement appropriate controls to protect their organization’s assets.
Information security professionals
CIM Intel Database can help information security professionals monitor for potential breaches or data leaks that could impact their organization. This can enable them to take timely action to prevent or mitigate the impact of these incidents, such as implementing additional security controls or notifying affected individuals.
Private individuals
End users who are customers or employees of a company that has experienced a data breach may benefit from the CIM Intel Database by being able to check whether their personal data has been compromised. This can help them take proactive steps to protect their accounts and personal information, such as changing passwords or monitoring for suspicious activity.
End users who are concerned about the security of their personal information online may use the CIM Intel Database database to monitor for any potential data leaks or breaches that could impact them. This can help them stay informed and take proactive measures to protect their online accounts and personal information.
Business model
SaaS Subscription
Customer’s analyst users receive access to the CIM Intel Database online. This enables analysts to create their own queries, gather information, and correlate data within the CIM Platform as well as with other third party sources.
SaaS Subscription with Analyst Services
CIM analysts do the heavy lifting for you. Customer’s analyst users explain the queries and context to CIM professionals, who gather information, correlate data, and publish reports.
Subscription - Raw data feed (with API)
CIM can integrate its intel database feed into customer’s platform, so queries can be run automatically and Background Check Reports generated for large databases of employees or clients.
CIM partners with distributors, vendors of OSINT data services
Cybersecurity Intelligence Services
CIM provides valuable information to cybersecurity intelligence services providers by helping them to identify potential threats and vulnerabilities. CIM provides intelligence on emerging threats, threat actors, and their tactics, techniques, and procedures (TTPs). This information can be used to develop threat intelligence feeds and to identify new patterns of attack. CIM data services also provide early warning alerts and threat notifications to help organizations proactively defend against cyber threats.
Background Check Services
CIM data services enhance the accuracy and completeness of background checks by providing access to a wide range of publicly available or hidden information. This information provides additional insights into an individual’s character, reputation, and behavior. CIM helps to identify potential red flags, such as criminal records, lawsuits, incriminating behavior, or negative media coverage, that may not be included in traditional background check sources.
Due Diligence Services
CIM provides valuable insights into the target company or individual, helping due diligence services providers to identify potential risks and liabilities, including identifying negative media coverage, regulatory violations, or other reputational issues that may impact the target’s business operations or financial performance. CIM provides information on key stakeholders, such as board members or executives, and their affiliations with other companies or organizations, helping to identify potential conflicts of interest or other compliance issues. CIM data services can help improve the accuracy and effectiveness of due diligence processes by providing a more comprehensive and detailed view of the target company or individual.
Cybersecurity Vendors
Cybersecurity vendors offer CIM CTI services as part of their broader suite of cybersecurity solutions.
Threat Intelligence Providers
Specialized threat intelligence providers focus specifically on collecting and analyzing threat intelligence data.
Managed Security Service Providers
Managed security service providers (MSSPs) offer CIM CTI services as part of their broader managed security services.
Benefits to OSINT Data Service Vendors
Additional revenue streams
Resellers can add CIM Intel Database service to their portfolio, which can create additional revenue streams for their business.
Higher quality (and quantity) of service
Without compromising on false positives
Competitive advantage
Offering CIM Intel Database service can give resellers a competitive advantage by providing their customers with a comprehensive suite of cybersecurity services.
Improved customer satisfaction
By providing CIM Intel Database service, resellers can improve customer satisfaction by offering a more comprehensive solution to their cybersecurity needs.
Access to advanced technology
Through CIM Intel Database, resellers can gain access to advanced technology and tools that are necessary for collecting, analyzing, and presenting OSINT data to their customers.
Scalability
CIM Intel Database service can be easily scaled up or down to meet the changing needs of resellers and their customers, providing them with greater flexibility and agility in responding to cybersecurity threats.
Reduced costs
Resellers can save costs associated with developing and maintaining their own OSINT data service by partnering with CIM Intel Database.
Target Markets
Enterprise
Large corporations and organizations of all types and sizes are prime customers for CIM CTI data. Enterprises can use CTI data to identify potential cyber threats, improve their security posture, and respond to security incidents.
Government agencies
Government agencies at the federal, state, and local levels can use CIM CTI data to protect critical infrastructure, safeguard national security, and respond to cyber threats.
Managed Security Service Providers (MSSPs)
MSSPs offer managed security services to their customers, including CTI data feeds and analysis, to help improve the security of their networks and systems.
Information Security Consultancies
Information security consultancies offer cybersecurity consulting services to their customers, including CTI data feeds and analysis, to help them improve their overall security posture.
Financial institutions
Financial institutions, including banks, credit unions, and investment firms, use CIM CTI data to protect their networks and customers against financial cyber threats, such as fraud, money laundering, and identity theft.
Cyber Insurance Companies
Cyber insurance companies use CTI data to assess the risk of insuring businesses against cyber attacks and to determine the appropriate insurance premiums.
Law Enforcement
Law enforcement agencies use CTI data to investigate cyber crimes and prosecute cyber criminals.
Litigation
Lawyers representing clients in cybersecurity-related litigation may use CIM threat intelligence data to build a case against a defendant or to defend against allegations of cybercrime.
Compliance
Law firms working with clients in regulated industries, such as healthcare or financial services, may use threat intelligence data to help their clients comply with industry-specific cybersecurity regulations and standards.
Due Diligence
Consulting firms and lawyers involved in mergers and acquisitions may use threat intelligence data to conduct cybersecurity due diligence on potential targets, assessing their cyber risks and vulnerabilities.
Insurance Claims
Attorneys representing clients in cybersecurity insurance claims may use threat intelligence data to support their clients’ claims by providing evidence of cyber threats or attacks.
Risk Management
Lawyers may use threat intelligence data to help their clients identify and mitigate cyber risks, and to develop risk management strategies to protect against future threats.