


Threat Intel and Security System Integrators
Threat intelligence is a critical aspect of modern cybersecurity, providing security system integrators with insights into potential threats and vulnerabilities that can help them protect their products and their customers (an sell it as an add-on service). However,...
Military use cases & risks of rugged BESS (Battery Energy Storage Systems)
There are several military use cases for rugged battery energy storage systems, including: Mobile Power Generation: Rugged battery energy storage systems can be used to power mobile generators used in military operations. These batteries can provide a reliable source...
Vulnerability Remediation Cost and Dollar Value Calculated
All the customer needs to do is provide their primary domain name and consent to the service. During the test, we examine possible vulnerabilities of the [example].com domain. The analysis includes the examination of Account Takeover (ATO, Breached Credentials),...
How would lawyers best use cybersecurity services?
Law firms use cybersecurity services to protect sensitive client information, financial data, and other confidential information from cyber threats such as hacking, malware, and ransomware. Law firms handle a wide range of sensitive and confidential data, including...
Operational technology (OT) systems are generally considered to be more vulnerable to hacking than information technology (IT) systems
Operational technology (OT) systems, which are used to control and monitor industrial processes, are generally considered to be more vulnerable to hacking than information technology (IT) systems for a few reasons: Age and complexity of the systems: Many OT systems...
What is the work of a cybersecurity threat intelligence analyst?
A cybersecurity threat intelligence (CTI) analyst is responsible for collecting, analyzing, and disseminating information about potential and current cyber threats to an organization. The work of a CTI analyst typically consists of the following tasks: Collecting...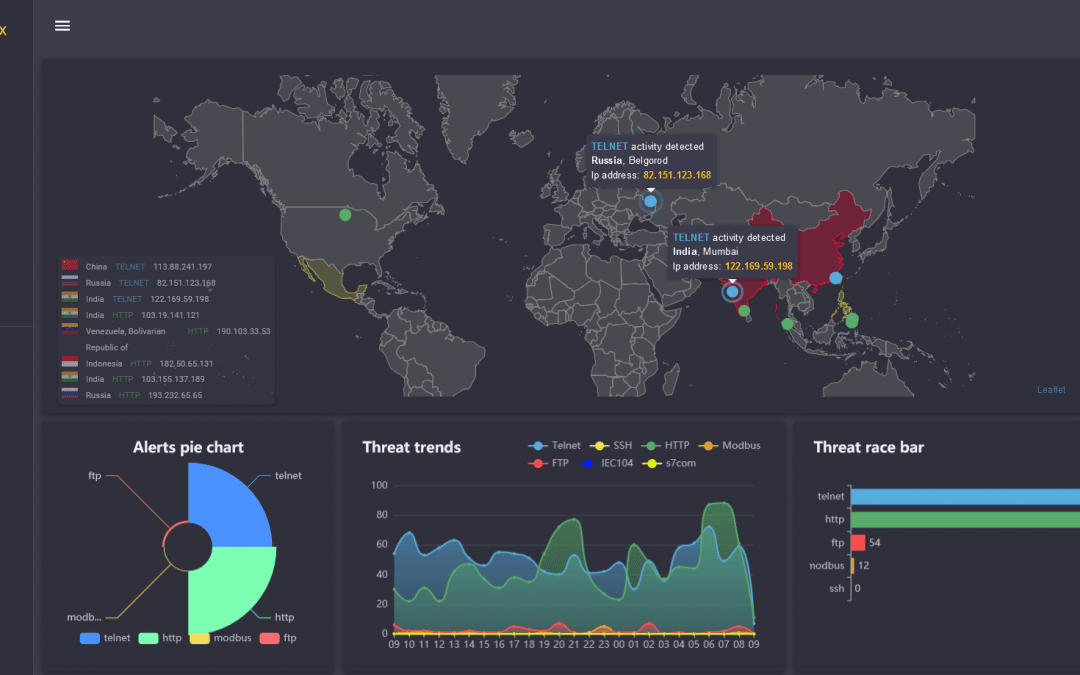
Cyber Attacks Against Industrial Control Systems (ICS)
The problem we solve is the constant fear about and the inability to accurately quantify risk regarding cyber attacks directed against industrial control systems (ICS). Operational Technology (OT) is much more vulnerable to hacking than Information Technology (IT)....
How many leaked breached credentials are there in the Dark web?
We integrate a constantly growing, proprietary, carefully curated 18-billion-plus database of breached credentials into our software products through our company Cyber Intel Matrix. It is difficult to accurately estimate the number of leaked or breached credentials...
